There are increasing reports among our clients of phishing attempts, including more targeted attempts (commonly referred to as spear-phishing attacks). In these attacks, emails might appear to come from high-ranking members of the company, or may appear as automated systems (voicemail, faxes, travel itinerary, order confirmations or invoices, etc.) They often can appear quite legitimate, mimicking the font, imagery, and even sometime signatures of legitimate users in order to fool you. These attacks tend to come in one of two varieties:
“I need this NOW!”
Often, attacks will appear to be emails from someone high up who needs login info, a wire payment, or some other form of money or access quickly, either to facilitate an order with a large client, or because they are in a rush. This is a common social engineering tactic, wherein people don’t want to get in trouble for holding up workflow, and so when asked to rush often forget to do due-diligence. To fight this, we often suggest people adopt a two-factor approach to these situations. If you’re not sure, call the person directly on the phone, or if you’re in the same office, go ask them if their request was legitimate. I promise, bothering someone is way better than wiring money without checking.
“Login Here!”
These emails appear to be automated and offer an invoice or attachment you weren’t expecting (or maybe you were, but this isn’t actually it). They may appear to come from Dropbox, or Microsoft Office, or Google, or some other company, and may look exactly like them when they ask you to log in. Once you do, links may even redirect you to the proper site, or an error page. Either way, they have your username and password, and can use those credentials to send emails as you.
Ways to Be Sure
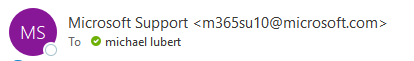
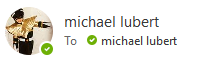
If you use Outlook, and if an email actually came from someone within your domain (the @something.com), you won’t see it listed, just their “Display Name.” If they come from outside, you’ll see the email address listed in the angled brackets after the name. It should become a routine to check these, because it takes a second and can save lots of headaches later.
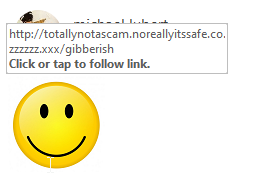
If you get an email with a link, hover over it to see if it looks legitimate. Often scam emails will buy look-alike domains, though many don’t care and will just take you to a URL that is obviously not where you’re going. Finally, if you’re ever in doubt, just forward the email to us, and we can verify it for you. We’re more than happy to do so, and being safe is infinitely better than being sorry.